Secure Computing and Kubernetes Master Node Protection (Ver 4.2 Update)
Dec 2022: HUB Security’s latest Secure Computing release addresses vulnerabilities in Kubernetes API master server protection
Since the launch of Kubernetes in July 2015, numerous enterprises have switched to the open-source container orchestration system to improve the efficiency of deploying, scaling and managing applications. Kubernetes is becoming an indispensable infrastructure for IT operations and DevOps teams. It's used to run all types of workloads, from development and test environments to mission-critical production applications. The Kubernetes standard is supported and promoted by leading technology vendors
including: AWS, Microsoft, Google, HCL, L&T, Mavenir , Redhat,, etc. to accelerate application modernization.
Using Kubernetes helps organizations migrate workloads from legacy on-premises and Cloud Foundry environments to modern Kubernetes-based platforms. The process is also repeatable, reliable and cost-effective, enabling organizations to reduce risk and complete migrations faster. The Kubernetes Master Node is the "front gate" of Kubernetes. It allows authorized users to perform any action on a Kubernetes cluster and potentially gain access to any sensitive data it manages. It provides a HTTP API that enables the communication between end users, external components, and different parts of a cluster. This makes the Kubernetes API server an extremely valuable target for attackers and a top priority for security strategy. Since Kubernetes is fully API-driven, controlling and restricting who can access the cluster and what actions they are allowed to perform is the first line of defense.
HUB support for Kubernetes Master Node Protection provides solid, layered security that can help customers reduce costs and achieve faster TTM while deploying new applications. HUB solutions protect Kubernetes master nodes using a digital twin of a Kubernetes proxy within the HUB Confidential Computing Platform.
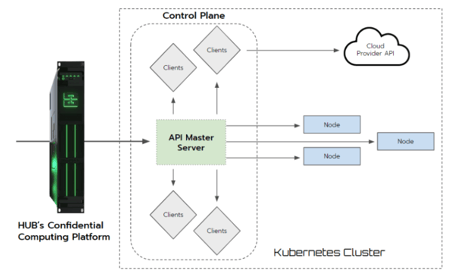
By establishing a secure encrypted channel between HUB platform's Kubernetes proxy twin and the original Kubernetes master node and applying NSA-recommended security best practices for post-boxing security, the Kubernetes master node's resources and actions are protected by HUB governance rules, blocking access through a network and packet filtering and role-based access control (RBAC) authorization enforcement. With one click (i.e., Wizard), the HUB platform creates role-based API endpoint groups based on Kubernetes permission roles and per provisioned Kubernetes namespace:
- View - View permissions for all namespace-level resources, except secrets
- Edit - View and edit permissions for namespace resources, excluding roles and role bindings.
- Admin - View and edit permissions for all namespace-level resources, including roles/role bindings
- Cluster Admin - All permissions for all resources in all namespaces
The API Endpoints in each group are adjusted to the role, per NSA best practices, to limit access to Kubernetes Master Actions and Resources. Each group of API endpoints is created with default out-of-box governance Authorization Rules to allow or deny access based on claims.
Conclusions:
Deploying the Secure Computing Platform running the latest software in front of a Kubernetes API Master Server improves the cyber protection of the Kubernetes Master Node. It enables role-based access per api of Kubernetes various endpoints. It also allows cluster tokens/access credentials to be kept secure and stored only on the HUB platform and not shared with clients.
Contributed to the post and release: Tal Shemesh, Senior product manager Ariel Caner, Senior product marketing manager

