Securing Edge Computing on 5G Networks
Secure Edge: Today’s Necessity, Tomorrow’s Problem
Edge computing is a distributed interactive computing system that relies on multiple trust domains. Within this kind of computing environment coexists multiple entities which require identity validation under a single trust domain all while entities mutually authenticate each other among multiple trust domains. This spells out a host of security concerns when it comes to edge computing, such as:
- Insecure environments for mobile edge computing on 5G networks
- Software that controls the Virtual Radio Access Network (vRAN)
- Open RAN (ORAN)
- 3rd-party value added applications
- Applications running on a commercial-off-the-shelf (COTS) hardware
The Role of Secure Edge Computing
At HUB Security we believe that confidential computing has the potential to solve a host of security issues that come along with 5G, AI/ML and IoT processing. With the help of hardware-based trusted execution environments (TEE), highly sensitive data can remain protected in memory until an application requests it to be decrypted for processing. With secure cloud computing, organizations can:
- Protect Sensitive Data – Extend cloud computing benefits to sensitive workloads for a more agile and accessible public cloud platform.
- Safeguard Intellectual Property – Trusted execution environments can also be leveraged to protect sensitive IP, business logic and analytics functions.
- Secure Cloud Collaboration – Collaborate with partners on new cloud solutions by combining sensitive data with another company’s proprietary calculations.
- Eliminate Cloud Vulnerabilities – Choose the cloud provider that best meets technical and business requirements by leveraging cloud computing services.
- Protect Edge Data in Transit – When used as part of distributed cloud patterns, data and application at edge nodes can remain protected.
HUB Security’s Zero-Trust Approach
HUB Security’s multi-core zero-trust confidential computing platform that provides end-to-end protection of secure edge environments for a wide-range of industries including finance, healthcare, and energy sectors.
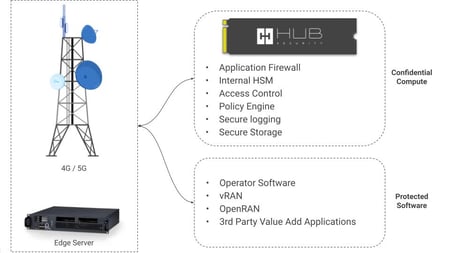
The HUB Vault is an ultra-secure hardware and software confidential computing platform, designed to protect your most valuable legacy systems and applications. The programmable and customizable multi-core confidential computing platform enables companies a simple, flexible, and scalable digital transformation to the cloud, regardless of a legacy model.
Protection From the Center to the Edge
Hardware security modules safely store secure keys, payments, and other business applications in an isolated environment. The right HSM should be built for sensitive and complex approval flows, such as secure access to critical infrastructures, payments, asset transfers, code signing, and identity management.
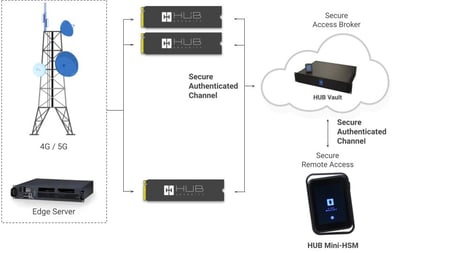
The HUB Vault HSM is a confidential computing platform, designed to provide security and privacy for your most sensitive organizational applications and data while in transit. The programmable and customizable multi-core Vault HSM enables companies a secure, fast and flexible environment to execute valuable AI applications, as well as general computing applications.

