Zero-Trust Confidential Computing for Legacy Systems
AS/400, iSeries and IBM zSeries Mainframe
Traditionally, security models operate on the assumption that everything inside an organization’s network should be trusted. Legacy architecture provides an additional layer of security with many benefits. At HUB Security we do things differently, especially when it comes to protecting legacy systems.
HUB Security’s multi-core zero-trust confidential computing platform that provides end-to-end protection of legacy systems, such as the AS400 and Mainframe etc.
HUB Security Zero-Trust Architecture
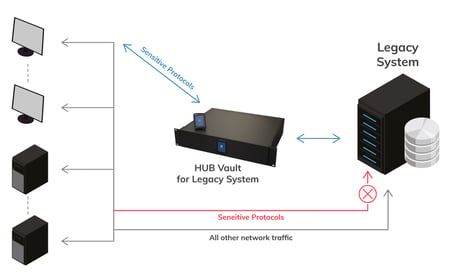
The HUB Vault is an ultra-secure hardware and software confidential computing platform designed to protect your most valuable legacy systems and applications. The MultiCore confidential compute platform enables companies the highest level of hardware based security to protect from the most sophisticated hacking through sensitive protocols.
Protection From the Inside Out
At HUB Security, we run on the core principle: 'Never trust, always verify'
- Legacy Systems such as AS/400, iSeries and IBM zSeries Mainframe
- No Legacy Modifications Required
- Transparent to Legitimate Users
- Safeguards Against External Attacks
- Safeguards Against Internal Attacks
- Modular and Easy to Configure
- Secure Logging
Common Vulnerable Protocols of Legacy Systems
- SMB
- FTP
- ODBC
- Telnet

