Confidential Computing & Multi-cloud – Why and How?
Confidential computing and multi-cloud seem to complement each other perfectly and lead to enhanced cybersecurity.
Multi-cloud strategies allow enterprises and organizations to choose from various cloud services offered by different providers. There are several significant advantages to doing this:
Specialization: Certain cloud platforms may better suit specific tasks or workloads.
For example, cloud providers may offer lower-cost storage, more powerful computing instances, or specialized analytics and machine learning.
Cost and financial leverage: Multi-cloud deployment allows organizations to leverage the most cost-effective services and negotiate with cloud providers.
Availability: Although cloud providers offer extensive high-availability options across data centers and regions, outages can occur. Deploying the same service across multiple clouds provides greater resilience and broader disaster recovery and business continuity options.
In addition, deglobalization and concerns about data sovereignty are driving companies and organizations toward multi-cloud architectures. It is therefore predicted that enterprises will increasingly adopt multi-cloud architectures in the coming years. According to The Flexera 2022 State of the Cloud Report survey, 89% of companies pursue a multi-cloud strategy for different reasons (geopolitical, technical, vendor diversification), but this comes with added complexity in connecting, securing, and monitoring the environment. 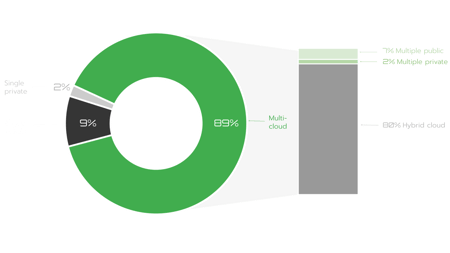
Source: Flexera-State-of-the-Cloud-Report-2022 CISCO’s CSO has recently predicted that In the near future, we will see new multi-cloud frameworks, such as sovereign clouds, local zone clouds, and zero carbon clouds. They will enable more private and edge cloud applications and services and introduce a new multi-cloud operating model. According to Flexera, 48% will use multiple public and private clouds, 31% of enterprises will use public clouds, and at least one private cloud. 12% of others will use one public cloud and multiple private clouds. So, one can conclude that the number of private clouds will continue to increase.
The question that arises is how companies and organizations will secure private clouds, especially the decentralized, standalone ones. One emerging solution is in the form of Confidential Computing. Its protection is assured over a distributed computing framework, as it can unconditionally guarantee the integrity and confidentiality of programs, applications, and data processing. When deployed in a multi-cloud environment, Confidential Computing promises a whole new vision of distributed security, enabling new guarantees and new privacy-friendly workloads and services.
The attestation and encrypted "handshakes" between programs and their computing platforms ensure a secure computing environment: data at rest, in transit, and, most importantly, in use. In addition to enabling verifiable security properties, Confidential Computing reduces security costs by replacing ineffective protections with more effective ones that cover a wider area. With Confidential Computing practices in place, applications become more secure and even allow multiple sites to work in a multi-cloud environment, with some noticeable advantages: Collaborative machine learning and data sharing: Confidential Computing allows many different entities to pool training and analytics data without disclosing it to any party in the pool or a trusted third party.
A related application is selective, policy-driven data sharing often called data sparsity applications. Secure Kubernetes management: Confidential Computing allows you to run your applications in a multi-cloud environment while ensuring that cloud providers cannot view or modify your data. Privacy-protected data processing provides confirmable rules to enforce specific government regulations or legal requirements, even outside the boundaries of the jurisdiction (e.g GDRP). Confidential Computing can ensure that the processing of sensitive data, follows strictly enforced policies wherever the data is processed. A sovereign cloud can be set up in a data center in any location and ensure absolute privacy compliance for data originating in another jurisdiction.
Secure hardware-based execution environments: Among the fundamental capabilities of Confidential Computing is the ability for organizations to offer protected critical services and protected, policy-driven data access anywhere in the cloud. In 2020, the Confidential Computing Consortium began the work of its technical advisory board to set standards. Companies such as Meta, Google, Huawei, IBM, Microsoft, and Tencent have participated. The idea at the time was that Confidential Computing, by isolating protected data, could allow different organizations to share data sets without having full access to them.
One of the goals of cloud providers that also offer Confidential Computing is to assure their customers that they can have peace of mind when the cloud provider itself has visibility into protected information. These are currently, and for the foreseeable future, the technological cybersecurity capabilities that enable the widespread use of the multicloud in all its forms and functions. Confidential computing and multicloud resemble the metaphor of the chicken and the egg, but the two trends seem to complement each other perfectly.

