Digital Twins for Confidential Computing
Definition
The prevalent definitions and usage of the digital twins concept are focused on representing some physical thing in the real world for monitoring and modelling. This original definition of the concept is inherently limited, as today’s “physical” asset is in many cases purely digital and virtual by itself (e.g. blockchains, AI, data, cloud computing). Furthermore, the current thinking focuses mainly on a single direction from the original to a twin, missing a world of interaction and mutual augmentation of capabilities and lifelike features, such as robustness, safety, security.
The New Digital
In our new world, here and now, the boundaries between physical and virtual are getting blurry. Surgeries are performed remotely via the internet, autonomous cars share their decision making brains with the cloud data centers, systems are distributed, virtualized and software-based as much as possible (like 5G ORAN). What is the twin then, when the original itself is purely digital? When does the behavioral AI model make and execute decisions that have a direct impact on the real world?
When does the physical thing become completely controlled by its digital twin? When everything becomes digital and interconnected, while digital processes become more valuable and critical, the temptation of malicious actors increases accordingly. The modern definition of a digital twin should include new responsibilities and capabilities. The new digital twin is a virtual entity that represents the original entity and provides additional capabilities above the exact representation of the original entity.
In the cyber security and confidential computing context, the original entity is a physical thing (appliance, OT controller, CPU) and a pure virtual digital thing (file, executable code, memory contents, DB). The digital twin can do much more than represent the original, by providing a multitude of confidentiality and security features and acting as the gatekeeper before and around the original entity.
The additional responsibilities and active decision-making capabilities raise the bar on digital twin cyber security requirements, such as accurate representation and behavior in the presence of attackers and vulnerabilities in the runtime environment of a digital twin. In regulated, critical applications, the digital twin itself should be the root of trust with ideally hardware-based trust to prevent attackers from influencing the original via the digital twin. A confidential computing environment that focuses on security includes several types of digital twins, which provide different levels of protection for the original, alongside a richness of capabilities.
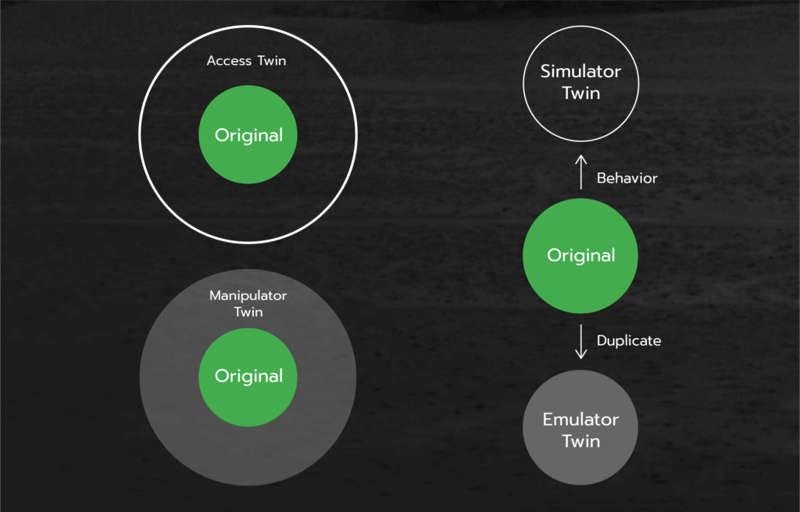
Confidential Digital Twins
These four types of digital twins can be combined as needed for the specific security and functional requirements. Furthermore, the above types are just a beginning in the twins’ family tree, as the possibilities are endless.Access Twin
Access control and isolation to compute infrastructure and resources is critical for any type of confidential and secure operation in the data center and on the edge, while hackers easily overcome the perimeter protections of the organizational network and insider threat is a very real thing. A service-based economy of applications and data providers creates a dangerous situation of sharing the same compute resource by multiple unknown and sometimes untrusted parties. The service provider’s system administrators have full access to the compute infrastructure (e.g. OS installation, memory dumps, BIOS updates, CPU microcode updates) and can override security configuration by intent or by mistake.
The access twin provides a virtual barrier between any type of the original sensitive entity (BIOS, OS, motherboard, BMC, VM, Hypervisor, application, etc.) and the outside world by presenting to the world the exact copy of the original entity communication interface. Therefore, all external actors see the normal API and interact with it as with the original entity direct API, while behind the scenes the entity’s digital twin checks everything coming in and everything coming out of the original and transparently executes identity verification, data filters, rules and policies on the requests.
The approved requests will be forwarded to the original entity and the rejected requests will be dropped with predefined responses (which can be nothing at all to prevent the attacker the knowledge of the twin's existence). The original entity does not know or care about the existence of its digital twin, as the original experience does not change at all. The twin core can be as simple or complex as desired for the specific original entity protection.
The one-to-one relationship between the digital twin and the original enables infinitely fine detailed control over the originals interface and by extension the operation. For example, BIOS firmware updates can be locked for approval by 3 specific employees and allowed only after image file cryptographic validation with manufacturer certificate and only during workday hours. Severe business consequences (like a Facebook DNS error) can be prevented by fully independent digital twins dedicated to the critical assets of the organization.
Simulator & Emulator Twin
Simulation and emulation are the “secret powers” of a digital twin. The simulation predicts the behavior of the original entity via simplified model, whereas the emulation recreates the exact virtual duplicate of the original. Both are used extensively in hardware and software development, especially for complicated large systems. Both bring substantial value to the cyber security domain, enabling the defender to check the end result of the incoming request before executing it in the real system (e.g. a sandbox). Bringing a digital twin to the original entity and adding an emulator or simulator twin to the access twin creates exponential benefits for security.
In our current reality of zero trust, constant change and anonymity, the enhanced Access Twin enables true validation of the incoming request impact on the original in real time and just in time to prevent disaster for the specific original entity. The ever increasing compute power in all devices from the production line robot and the industrial controller to the miniature PC and rack server, combined with specialized compute ASICs, enables the simulator/emulator twin real-time execution at the location of the original entity. The next generation ultra low latency communications (5G/6G, fiber) enable simulation/emulation execution in real time anywhere. Both trends together open a possibility for BYODT (bring your own digital twin) to secure real assets anywhere at all times.
Manipulator Twin
This twin type is an independent active self aware twin of the original. The manipulator twin isolates the original entity from the environment and proactively changes the incoming and outgoing data to keep the original safe even in the absence of access control rules. The following examples are applications of the manipulator twin concept:- Sensitive personal data obfuscation, like credit card and banking information. There is extensive regulation today on private personal information and strong enforcement by governments. The problem is that the enforcement and obfuscation usually happen in the repositories of the data after it is exposed on the cloud. Furthermore, this functionality requires changes in the applications or installation of software agents, which can be overcome by hackers. A digital twin with full knowledge of the original interface will catch the sensitive payload on the fly and remove it automatically and transparently to both the original entity and to the external malicious agents.
- Automated transparent encryption to prevent bugs/problems/omissions in the original entity from leaking information to the external world.
- Adjusting the values of the incoming data to prevent damage to the original entity, as in the Stuxnet example.
- Protection of critical disaster recovery backup for the organization data from ransomware attacks.
- Manipulation is an abstract concept applicable to any type of data and interface. The specific implementation is coupled with the original entity behavior and limits. Its power emerges from the intimate relationship and direct connection to the original entity. There is no going around the twin.

